The risks of cyber-attacks are growing more and more in terms of numbers and magnitude due to technology evolution and Geopolitical and macroeconomic context. It has become essential for the organizations to assess those risks and manage them in an effective and timely manner
The risks related to cyber-attacks have grown frenetic in last years fostered by technology evolution and recent worldwide events such as pandemic and warfare that have dramatically increased the use of information technology and included the digital world in the modern battleground.
Organizations are continuously and systematically exposed to cyber-attacks:
- 86% of organizations had at least one user who try to connect to a phishing site;
- 70% of organizations had users that were served malicious browser advertising;
- 50% of organizations encountered ransomware-related activity.

In this context it has become essential to assess in an efficient and effective manner the risks related to cyber-attacks affecting the organization as a whole in order to outline its Security Posture and implement suitable remediations actions.
A proper risk assessment allows the company to identify the most relevant and the greatest risks that it is facing and prioritize the interventions to manage risks; furthermore, it enables to identify the areas that are more vulnerable to the cyber-attacks and decide how to successfully protect them.
What are the most common and relevant cyber-attack risks?
Currently the most common and relevant cyber-attacks are ransomwares and other malwares, DoS and DDoS, phishing and password attacks (e.g. brute-force).
Cyber-attacks can potentially target each area of the organization given the multiple and wide attack surface that nowadays companies have, such as:
- Internet surface (e.g. websites, web applications, connected products, cloud services) which are potentially targeted by all over the world; smart devices like refrigerators or cameras can be easiliy hacked if not properly hardened and cloud breaches have surpassed on-premise attacks.
- Processes and Organizations exposed to different type of attacks, including social engineering and phishing; so called “CEO Fraud” attacks (also known as Business Email Compromise) created a market of 26 billion dollars.
- Solutions and technologies, exposed to multiple type of vulnerabilities (e.g. malware attacks, zero-day vulnerabilities); suppliers with their solutions are increasingly becoming a vector for cyber attacks (e.g. SolarWinds hack).
 Among all the various attack scenarios, ransomware is one of the most feared: global ransomware damage costs are predicted to exceed $265 billion by 2031.
Among all the various attack scenarios, ransomware is one of the most feared: global ransomware damage costs are predicted to exceed $265 billion by 2031.
Usually brought in the company network by unaware and untrained employees clicking on link contained in phishing emails, this malware is capable of encrypting the affected devices and making stored data unavailable. Unless the company pays a ransom to the cybercriminals data will remain unavailable. After paying the ransom, the decryption key is supposed to be released by the cybercriminals to let the company have data back, but this does not happen often: that is why paying the ransom is never a good option.
What are the main cyber challenges faced by Organizations?
 1. Understand the cyber risk language
1. Understand the cyber risk language
While the business impact of a cyber attack involves top management and company executive boards, cyber security is a highly complex matter managed by technicians unable to effectively convey the concrete consequences of cyber risks.
 2. Continuous evaluation of always-changing threats
2. Continuous evaluation of always-changing threats
Cyber risk is not a static exercise valid for long time (e.g. ransomware wasn’t a daily topic of discussion few years ago), it’s a dynamic journey that requires continuous evaluation to cope with always new risks.
 3. KRI/KPI highlighting main risks and reporting
3. KRI/KPI highlighting main risks and reporting
The amount of information generated by cyber security platforms (e.g. SIEM, IDPS, EDR, NGFW) can overwhelm any analysis and hardly translates into few key actions; top management needs few actionable KRIs/KPIs.
4. Driving of investments based on cyber risks
cyber risks
The evaluation of the budget for cyber security is often a subjective and highly hypothetical exercise, detached from real risks that would require timely intervention; the prioritization of investments on looming risks enables Organization to focus on solutions that provide value for money.
Cyber Risk DIVE (i.e. Deep Into Vulnerabilities and Exposures) is BIP CyberSec SaaS solution ensuing an efficient approach to cyber risk management, able to answer to all the challenges mentioned while speaking a language comprehensible from application owners to C-Level.
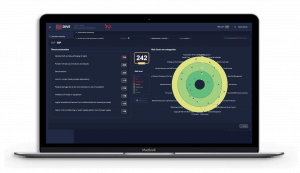 Cyber Risk DIVE to manage cyber risks
Cyber Risk DIVE to manage cyber risks
Leveraging +10 years of experience in the management of cyber risk assessment projects, BIP CyberSec defined a proprietary and e2e methodology to assess and manage cyber risks.
In order to have a thorough evaluation of cyber risks, our methodology identifies two perspectives and two dimensions of analysis:
1. Internal perspective
Cyber risk is evaluated as consequence of the AS-IS security practices within the Organization, which in turn are assessed from two dimensions:
- Process, Organization and Compliance:
This first and top-down dimension assess the existing processes as well as roles and responsibilities assigned for cyber security; it is performed via interviews with identified stakeholders (e.g. CISO, CIO, HR, Process Owners) and identifies common security weaknesses (e.g. lack of awareness, unclear accountabilities), regardless of the security posture of specific applications/systems.
- Solution and Technology:
This second and bottom-up dimension assess cyber security technologies and architectures as they are applied for the secure design and protection of applications/systems (e.g. integration with SAST/DAST platforms, hardening in line with security benchmarks, monitoring of suspicious events); such assessment if focused on a selection of identified business critical applications and complements the high-level and cross-applications evaluation performed via the Process, Organization and Compliance dimension.
The two internal dimensions are enriched with an external assessment performed via our Ethical Hacking team: the Digital Footprint.
2. External perspective (Digital Footprint):
This external and passive assessment (i.e. no impact on Business Operations) evaluates the AS-IS security posture of the Organization from two dimensions, people and technology:
- People:
Starting from a list of key people (e.g. C-Level names and email addresses) our experts scan the Dark Web to find if any information (e.g. passwords) is sold or discussed, this being a symptom of imminent cyber attack.
- Technology:
Starting from a list of Internet exposed URLs/FQDNs, our Ethical Hacking team tests the secure configuration of company’s systems (e.g. Web servers and web application layer) to identify poor configurations (e.g. unsecure and not needed ports open, information gathered that could enable an attacker to spot vulnerabilities).
As result of our comprehensive assessment, we are able to share with Organizations a complete Gap Analysis report and resulting roadmap, listing a prioritized set of actions to mitigate the identified risks.
Cyber Risk DIVE platform is the enabler of this continuous risk management program, empowering Organization to assess in few week their security posture and keep track of needed initiatives. Feel free to reach our experts to understand how we can protect your business.