Why protecting digital identities has become a priority for every business: attack modes and solutions to defend against them.
In today’s increasingly digitalized and networked environment, all companies are facing an ever growing attack surface.
In this scenario our Digital Identities, in addition to representing a set of data and attributes, are a real passe-partout that grant access to every corporate resource and allow to perform tasks, based on assigned permissions.
They are a prime target for any kind of malicious attacker because:
- They are easy to compromise (how, we shall find out in a bit)
- They represent the key in breaching a company’s digital environment circumventing perimeter defenses (e.g., firewalls)
Nowadays when work is becoming more decentralized, hybrid and full cloud models are on the rise, the boundary is set by the digital identities themselves, which go beyond the scope of the company’s datacenters.
The only way to guarantee that all of the infrastructure and apps are safe is to use an Identity-Driven security strategy.
Attack methods to digital identity theft
The most common scenarios which, in the day-by-day management of digital identities, could compromise the company’s security are:
- Inadequate digital identity lifecycle management leading to their uncontrolled spread
- Lack of proper checks on the accounts that access corporate systems
- Inadequate controls over privileged permission assignment
To understand how to mitigate and address these issues, it is important to understand the main techniques that attackers (crackers) use to compromise digital identities.
The attacker’s goal is to gain access to private and confidential information, and once the identities and credentials of the associated users have been compromised, he often exploits their privileges completely unnoticed, even for extended periods of time. This allows an attacker to control critical business applications or systems, even to the point of compromising daily operations.
Popular attackers’ methods to steal digital identities
The methods used for digital identity theft are several: from attacks that
target specific technological vulnerabilities to Social Engineering techniques that exploit people’s emotions in hopes of obtaining information vital to the attacker’s success.
With these aspects in mind, the most common methods that attackers use are:
- Interception: passwords can be passively intercepted (sniffing) or actively intercepted (spoofing, man-in-the-middle) when they are transmitted, especially if cryptographic protocols (SSL/TLS) are not properly used to protect data in transit.
- Brute-force attacks: they consist of repeated attempts aimed at identifying user passwords. They are usually performed with the help of software that automates this type of activity (i.e., hydra, Hashcat, JTR) also using password dictionaries, or trying to input a single, fairly common password on all usernames in an organization (password-spraying). Depending on the length and complexity of the passwords used, it can take an attacker from a few seconds to much longer periods to discover it.
- Social Engineering: the attacker uses people’s trust and social interaction to trick the user into revealing credentials or other sensitive information. A common example is the attack called SIM swap: it targets two-factor authentication performed via SMS OTPs. Another example is Phishing attack: apparently legitimate emails and SMS messages that actually hide malicious content and links.
- Credential Search and Theft: it can be manual or automated, and it targets passwords that are hard-coded inside script and software’s source code (written during its development), or stored in an insecure way (e.g., unencrypted).
- Key Logging: it is done through a malware, or a physical device used to record the sequence of keystrokes that are typed while entering a password.
- Credential Stuffing and Manual Guessing: it exploits the bad habit of reusing the same password on multiple services or using passwords with personal data (i.e., date of birth or other personal attributes). They consist of trying to access an account using credentials from previous data breaches that were sold or shared on the deep web.
- Physical methods: it leverages physical access to locations, peripheral and unattended or lost devices. The evil maid attack is a classic example: an external attacker with physical access to corporate premises can hide physical key loggers inside offices or attempt to compromise unattended devices if they are not properly protected with encryption, automatic lockout time-out, video surveillance, and physical access control. As well as the simple Shoulder Surfing (i.e., observing/spying on someone while he is typing a password).
Implications
Proper protection of digital identities in the corporate environment can make all the difference from a security and safeguarding of assets standpoint, especially in the current context of rising security costs and attack incidents.
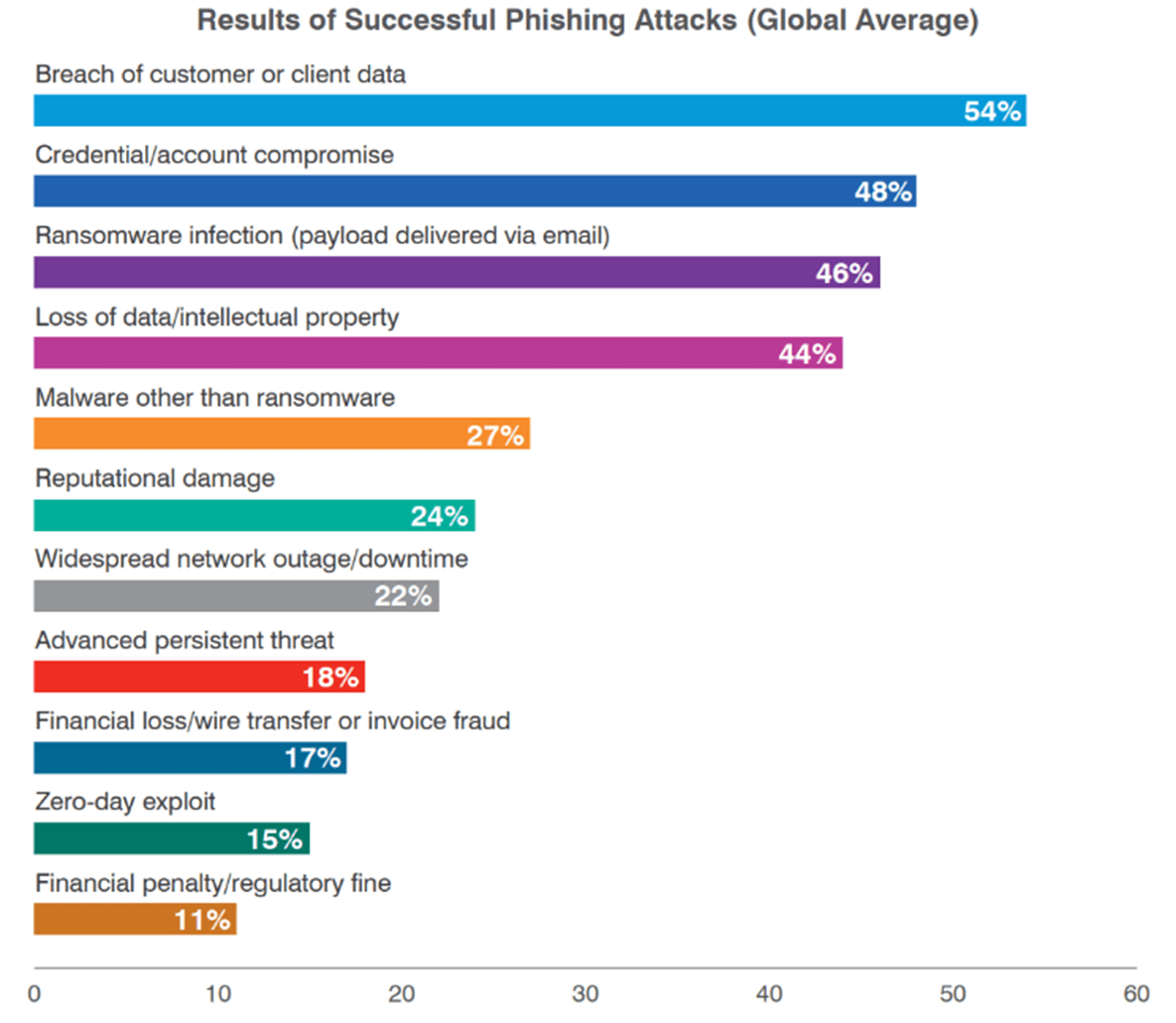
From 2022 State of the Phish – Phishing Attacks results
In fact, the cost of cybercrime is in continuous and perpetual increase: the latest Clusit 2022 report estimates worldwide damage from cybercrime to be 4 times Italy’s GDP just in the 2021.
According to Verizon’s 2022 Data Breach Investigations Report, 82% of data breaches include human factors and inadequate management of digital identities among the triggers that enable exploitation of key attack methods.
The simple use of phishing techniques (the attack vector with the highest success rate) if brought to completion, can result in very serious consequences for any company, as highlighted by Proofpoint’s 2022 State of the Phish report.
Furthermore, during a recent analysis by Gartner Peer Insights and Radiant Logic, 61% of respondents answered that the company in which they work still sees Identity management as something overly time-consuming and costly to be effectively managed, not realizing that, in case of an attack, the costs would most likely be extremely higher.
Which digital identities should be protected?
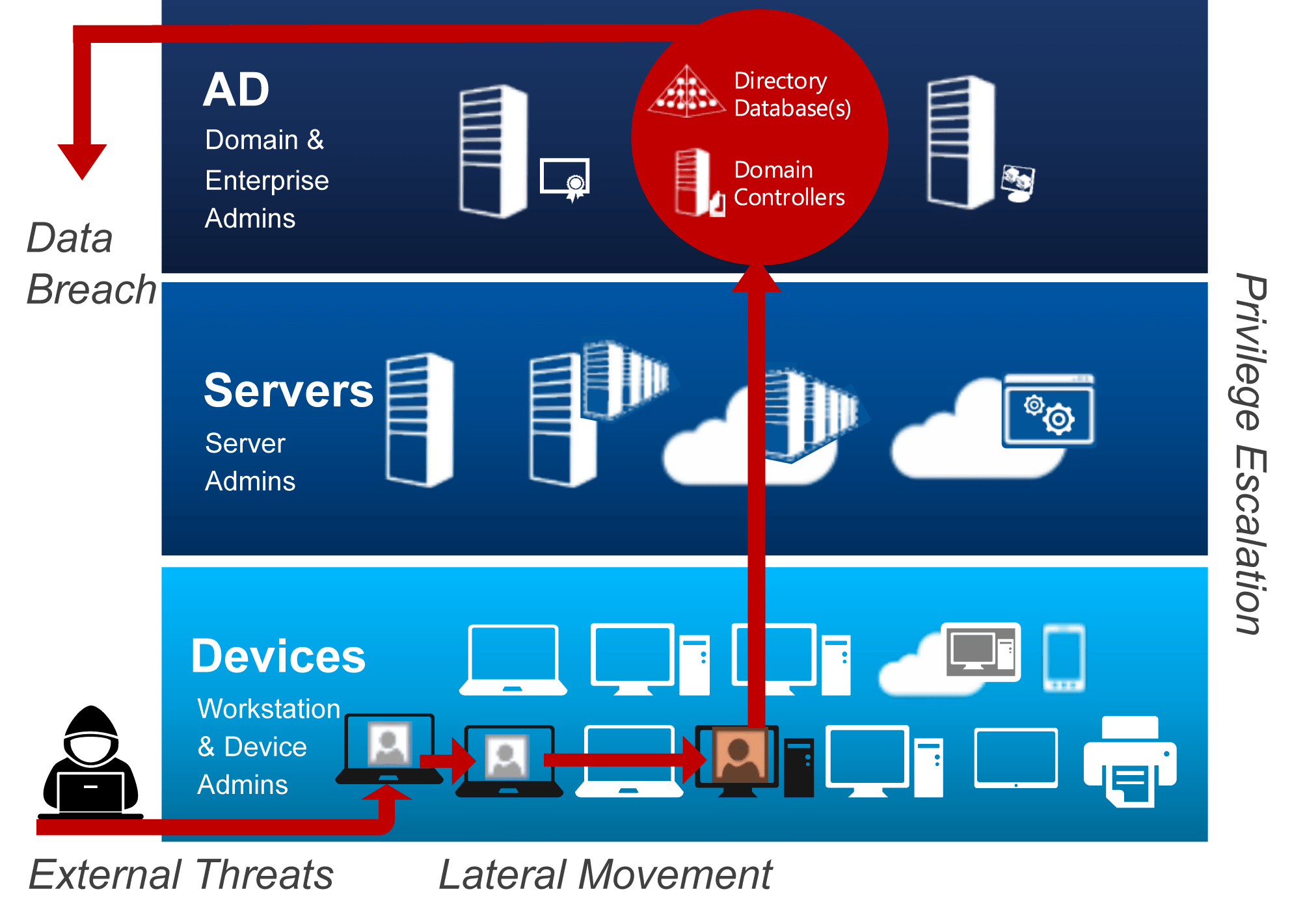
Regardless of their privileges and permissions, all digital identities represent an entry point to data and corporate systems, and must be properly protected.
In fact, being able to compromise even an identity with minimal permissions can be enough to trigger a range of irreversible consequences. The attacker could carry out lateral movement activities by taking possession of other credentials and gradually compromising more and more devices and accounts. In this way, through privilege escalation, he could take control of critical business systems (i.e., Active Directory), with easily imaginable consequences.
Digital identity Protection with BIP CyberSec
BIP CyberSec has developed an approach that helps its customers address their needs in a modular, structured, vendor-neutral manner. Starting with the definition of an Identity and Access Management (IAM) strategy, we are able to provide a 360-degree overview that is useful for creating the foundation that allows innovation and improvement of processes and technologies.
We use proprietary assessment tools, which we personalize according to the context of our customers, to evaluate the actual maturity level in the IAM domain and consequently, identify and promote process and technology improvement actions.
Our digital identity protection services cover all key areas within IAM.
Finally, how can we best protect our companies from digital identities threats?

The protection of digital identities and the adoption of an IAM strategy are essential
to ensure the security of personal information and protect organizations from threats and cyber risks.
BIP CyberSec‘s approach to identity and access management focuses on a comprehensive analysis of organizations’ processes, procedures, technologies and risk exposure. All these streams combined provide an E2E view of the company’s security condition, enabling us to design and implement an effective roadmap of initiatives.
To learn more about how we work and how we help our customers to effectively protect digital identities, visit our page or contact us for a consultation with our experts.